Stale User Accounts
$500 CAD
Are your staff actually using the accounts you've set up for them?
This report identifies stale user accounts, covering:
- users who haven't agreed to the EULA,
- users who have never logged in,
- users with no logins in a timeframe you specify,
- users with concurrent logins,
- infrequently used accounts,
- if you're using 2FA, user accounts with no security key,
- median days since most recent login, and
- average logins per user.
What's included?
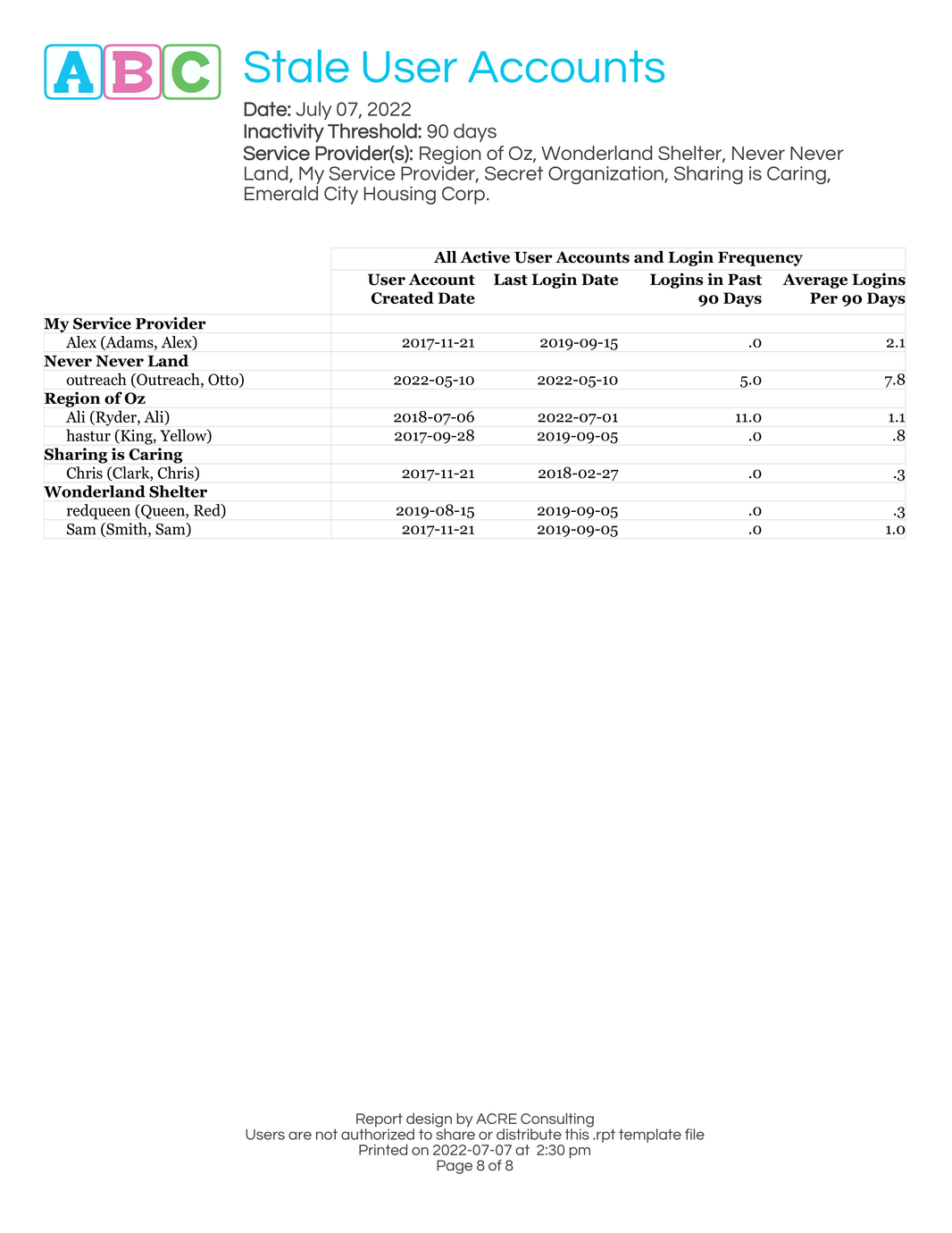
This 8+ page report aggregates data about user accounts, with the following breakdowns:
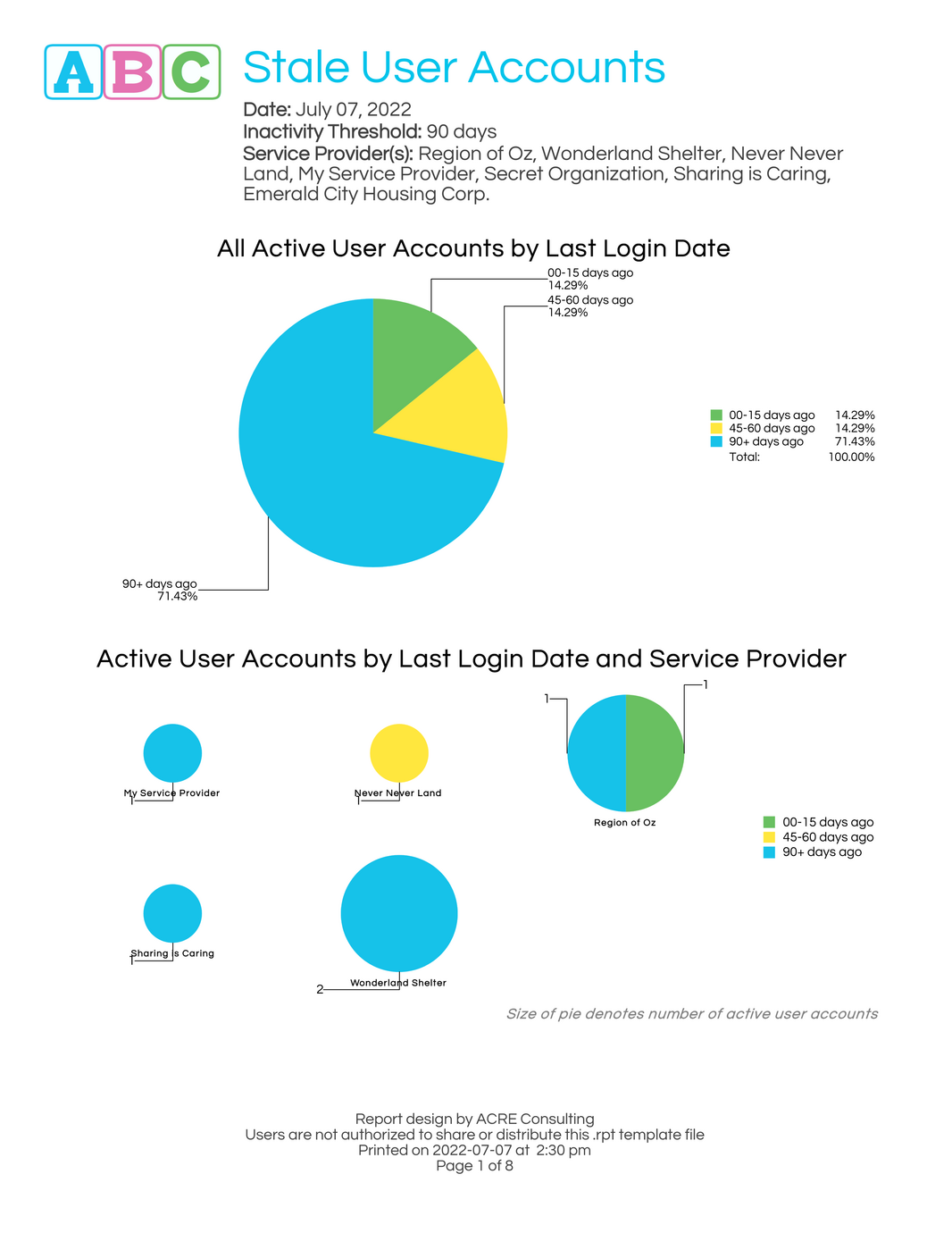
- Overall percentages of users by most recent login date, and breakdown by service provider
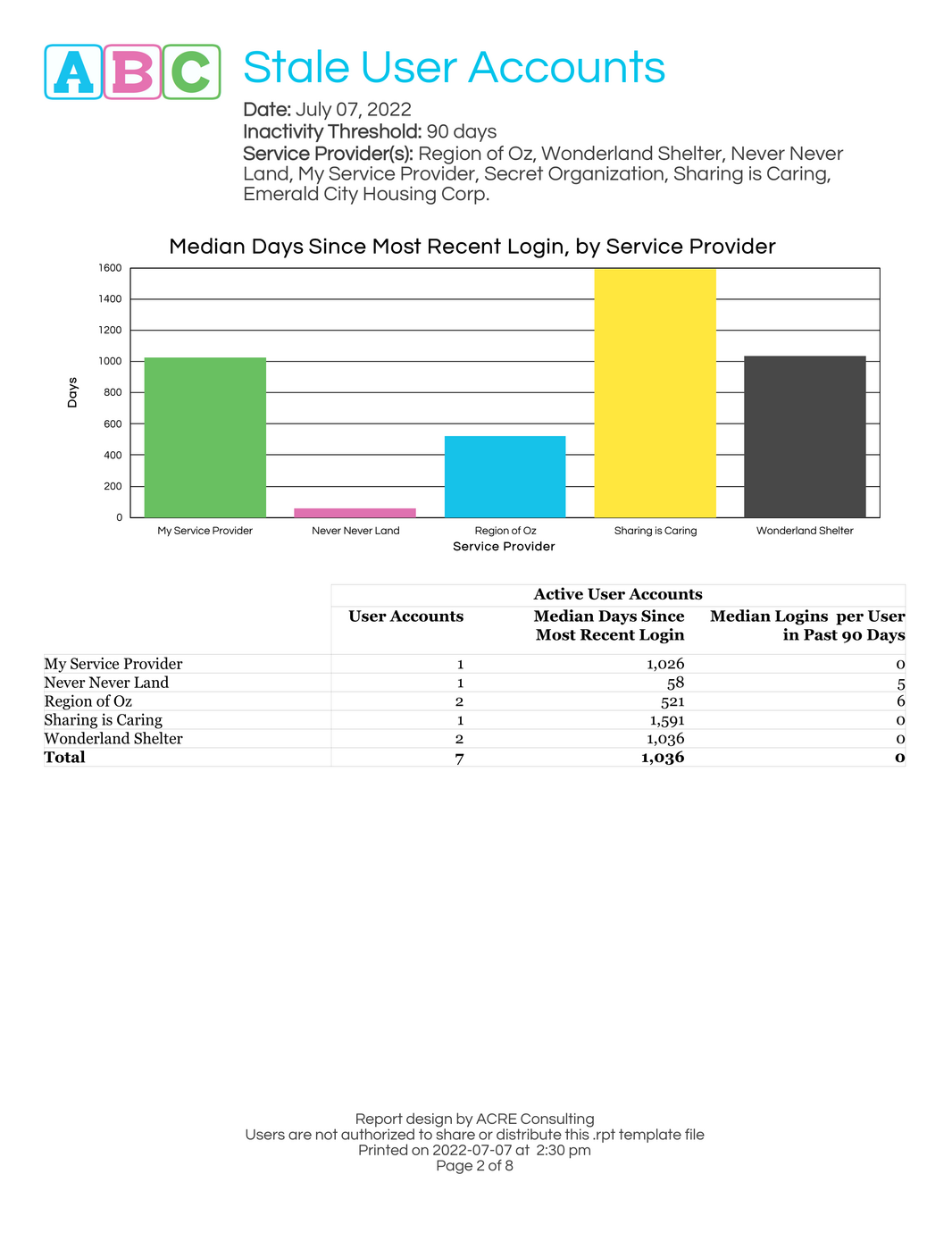
- Median days since most recent login, by service provider
- Median logins per user in the reporting period
- User accounts with no EULA
- User accounts who have never logged in
- User accounts with no recent logins
- If using 2FA, user accounts with no security key
- User accounts with concurrent logins enabled
- Infrequently used user accounts
What is a stale user account?
Inactive accounts or accounts that have never logged in are also known as “stale” user accounts.
Stale accounts pose a security risk to organizations. Each one of these accounts offers a malicious actor an opportunity to gain access to your data. When stale accounts are unknown or unmonitored, a malicious actor can compromise one and remain hidden to IT staff.
Best practices and standards require that these accounts are removed or disabled within a set amount of time.
Think of it this way; imagine you run a kingdom in medieval times. Each account that is given out or created is a member of your kingdom that has keys to the city. A key (or account) could topple your entire kingdom, as other kingdoms or bandits (malicious actors) want to get into your kingdom to steal anything of value. The more keys (or accounts) you can remove from circulation, the more secure your kingdom is.
Frequently asked questions
Frequently asked questions
You've got questions? We've got answers.
This report should run on any version of HIFIS version 4.0.57 and higher.
This report will be maintained into the foreseeable future. If a software update causes it to stop working, or if we find an error, we'll update the file and let you know there's a new version available, at no additional cost to you.
The run-time varies depending on how much data is in your database, and how long a date range and how many service providers you select when running the report. However, we have tested the report with large data volumes and it runs quickly and efficiently.
- Service Provider(s)
- Start Date
- End Date
- Inactivity threshold (for user accounts)
Check out our README file.
Audit Boot Camp
A series of premium reports and materials expertly crafted to help you whip your data into shape.
You may also like:
ABC Rights Templates Usage
Audit Boot Camp
It can be HARD to keep your users, service providers, and rights templates straight. Who has which template? Which users have access to what service providers? This report is designed to help you answer these questions and manage that aspect of your system.
ABC Duplicate Clients
Audit Boot Camp
Hunt down those duplicate clients! This report uses advanced methods to identify potential duplicates, helping you identify duplicate clients with misspelled names, swapped middle-first names, and even matching aliases. You get to choose whether to include clients with Declined - Anonymous consent, and whether you want to expand your search to other Clusters. Improve your database's uniqueness today!
ABC Stale User Accounts
Audit Boot Camp
This report identifies stale user accounts, covering: users who haven't agreed to the EULA, users who have never logged in, users with no logins in a timeframe you specify, users with concurrent logins, infrequently used accounts, median days since most recent login, and average logins per user.