
In HIFIS 3, the strength of users' passwords didn't matter as much, because a user had to be at the physical computer in order to login, which meant they were on site at a service provider.
In HIFIS 4, that all changed. The default configuration for HIFIS 4 is that it's hosted on a website that anyone can access if they have the URL. Then all they need is a username and password.
The Olden Days
In the olden days (i.e. a few months ago), communities could set a default password (the factory default setting was 123456 as the default password). This default password was assigned to all new user accounts. When a user first logged in, they would be prompted (but not required) to change their password. But if a user never logged on, their password would remain the default one indefinitely. Also, any time a user forgot their password, the only way to recover it was to reset it back to the default password, and prompt the user to change it again.
To make matters worse, most communities have a policy governing usernames, so it's usually very easy to guess a username.
Users were also prompted for a "secret phrase." This was a knowledge-based authentication (KBA), like when a site asks you “Where did you attend high school?" or "What’s your favourite football team?" However, since users were just prompted for a "secret phrase," not the name of their first pet, this was particularly misused. All that was needed to reset the user's password back to the easy-to-guess password was to guess the user's secret phrase.
The Way of the Future
Recently (version 4.0.52.22), the HIFIS Development Team made substantial security enhancements to the way passwords work in HIFIS 4. (Yay!) This is on top of the existing two-factor authentication option which was implemented about a year ago.
First, there's no longer a default password. If your community's HIFIS server has email configured (another new feature!), HIFIS can also email the user directly, prompting them to create a secure password without the Administrator ever knowing what their password is, or having to keep track of it. You can also configure how many days the user has to create a password before the email link expires.

If you don't have email configured, HIFIS gives each user account a randomly generated, very complex, temporary password. For example, a password that HIFIS randomly generated for my test account was jOT)&aC?}YZm=h. (That's pretty complex! And way more complex than 123456...)
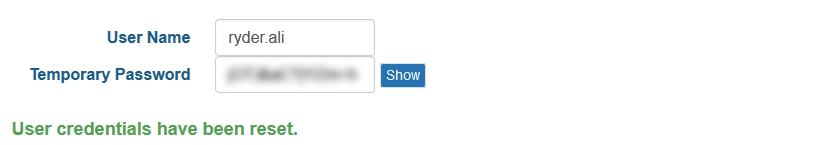
The secret phrase is also gone. When a user clicks the Forgot Password link, instead of entering their secret phrase, HIFIS will now email the user a password recovery link. If email isn't configured, a HIFIS Administrator needs to manually reset the user's password to an auto-generated temporary password.
Communities can also enforce password strength requirements. HIFIS Administrators could do this before, but since it requires configuration on the server, most communities didn't know that they could. For example, a common set of password strength requirements would read as follows:
Must be a minimum of 8 characters in length and must include:
At least one upper case letter (A, B, C)
At least one lower case letter (a, b, c)
At least one numbers (1,2,3)
At least one non-alphanumeric character (*,!,@)
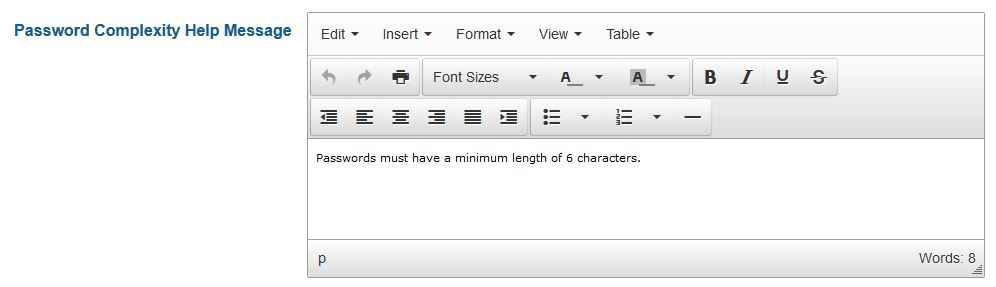
Now, there's customizable help text that informs users what the password strength requirements are (this didn't used to be an option).

Comments